Managing Windows version updates
This article explains how to manage Windows 10 or 11 version updates on managed devices with Miradore Management Suite.
Before you start
Read through the Getting started with patch management article and make sure these requirements are met:
-
Patch management is enabled in your Miradore license
-
You have access to modify files on the media master installation point
-
You have either administrator or security officer user rights in Miradore
-
You have installed and activated the Patch manager component
-
If you are upgrading devices from Windows 10 to 11, you must have MMS version 5.6.0 or higher.
Step-by-step guide to managing Windows version updates
-
Find and download the installation media (ISO file) of a new Windows version update.
-
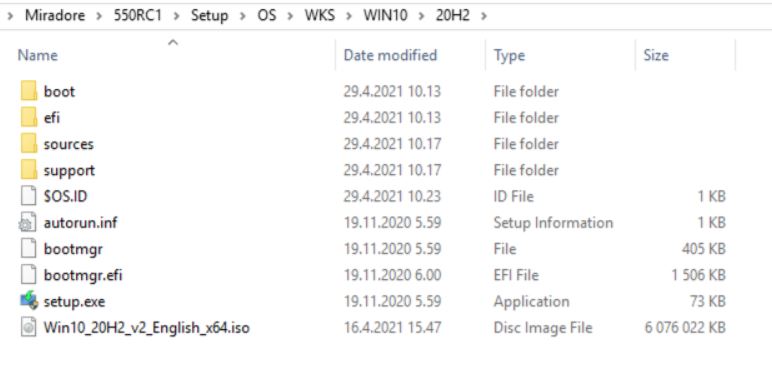
Extract the contents of the ISO file to the correct directory on the media master installation point. For example: Setup > OS > WKS > Win10 > 20H2. These files will be used when devices download the update from a network share installation point.
-
If you want to run Windows version updates for remote computers over HTTP(S) installation points, you must also place the ISO file to the same directory (see picture below).
-
-
Run the "GetOSInfo.CMD" script manually or wait until the next day (the script runs automatically every night).
The script analyzes the added update files and creates new Patch items to Miradore accordingly. -
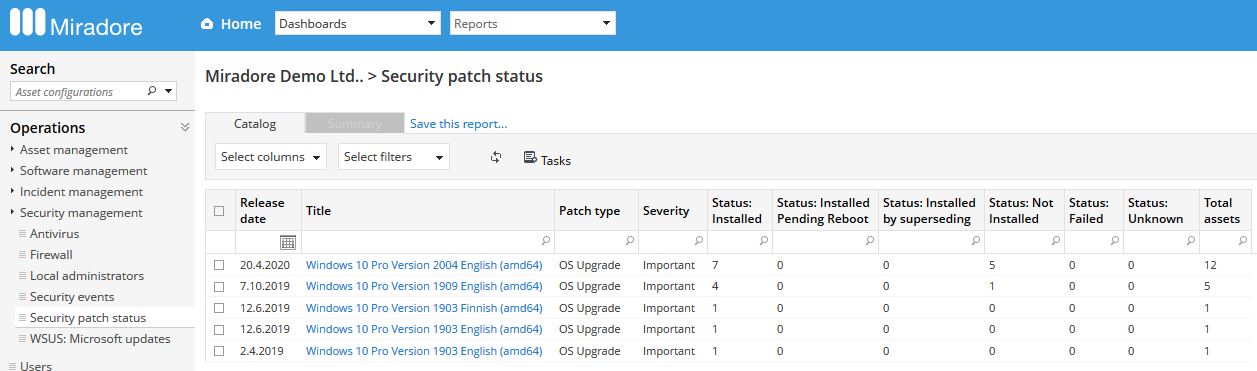
The updates will show up in the Administration > Feature settings > Patch management > Security patches view in Miradore Management Suite.
Tip: You can use "OS Upgrade" filter in the "Patch type" column to filter the view contents. -
Choose which devices are allowed or prohibited to install the update(s). You can do that manually using the view tools (Tasks > Tools > Approve patches...) or you can define automatic rules to process the updates.
-
You can configure a custom reboot message for OS upgrades in Miradore System settings > Main > Patch management. This message is shown to the device user if the update requires a computer restart.
-
-
Monitor the status of installations in the Operations > Security management > Security patch status view.
Define a custom reboot message
Administrators can define a custom reboot message in System settings > Patch management. The reboot message is shown to the device users if an operating system update requires reboot.
What happens at the managed device
A device executes the installation media over the network if it can connect to a network share installation point and there is no maximum bandwidth usage limit set for the asset's location item.
If a device can connect to a network share installation point, but the bandwidth usage is restricted, then the device first downloads the installation media to a temporary folder on C: drive and then runs the update locally. The temporary folder will be removed if the update succeeds.
If device connects to an HTTP(S) installation point, it always first downloads the ISO file entirely and then runs the update locally.
Troubleshooting
If the installation of a Windows 11 OS upgrade patch fails with the error "MOSETUP_E_COMPAT_SYSREQ_BLOCK", this means that the target device does not meet the requirements of Windows 11. In this case, Miradore will automatically max up the patch retry count for that device.
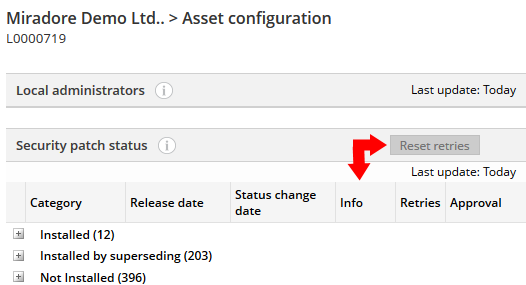
You can monitor the installations also through each Asset's Security tab. In the "Security patch status" table, you can see if the installation has failed, what is the error code and also the installation retry count. In the table header you can also find a button which lets you reset the retry count if the retry limit has been achieved already (see picture below). You can set the retry limit for failed patch and update installations in System settings > Patch management.
If you are having questions or concerns regarding the update, you can also try to seek help from Microsoft documentation which explains how you can rollback Windows updates and how long the pre-update version of Windows is stored in the Windows.old folder.
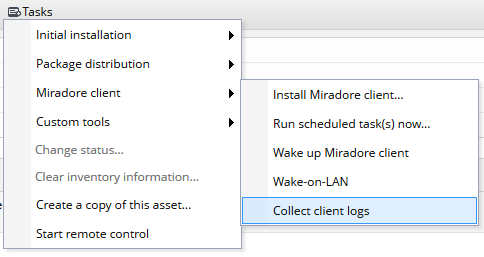
Miradore clients also write logs about the update installations which may be helpful in troubleshooting failed installations. The logs can be found from the Temp folder of Windows with the name "MD-OSUpgrade*.log". The easiest way to get these logs is to use the "Collect client logs" task which is in the Asset configuration items' Tasks menu.
See also
Getting started with patch management
Approving patches manually
Approving patches with automatic rules
Monitoring patch installations
Related to